Both dns poisoning and arp poisoning involves – Both DNS poisoning and ARP poisoning involve manipulating network protocols to compromise network security. These attacks can have severe consequences, ranging from data breaches to service disruptions. In this comprehensive overview, we will delve into the mechanisms, impacts, and mitigation techniques of both DNS and ARP poisoning.
DNS poisoning, also known as DNS spoofing, targets the Domain Name System (DNS) to redirect internet traffic to malicious websites. ARP poisoning, on the other hand, targets the Address Resolution Protocol (ARP) to link a malicious IP address to a legitimate MAC address, allowing attackers to intercept network traffic.
Definition and Explanation

DNS poisoning and ARP poisoning are two types of network attacks that exploit vulnerabilities in the Domain Name System (DNS) and Address Resolution Protocol (ARP) to redirect traffic to malicious destinations. DNS poisoning involves manipulating DNS records to map legitimate domain names to incorrect IP addresses, while ARP poisoning targets the ARP protocol to link MAC addresses to incorrect IP addresses.
In DNS poisoning, attackers gain control of a DNS server and modify the DNS records for a targeted domain. When a user attempts to access the domain, their DNS request is directed to the attacker’s malicious server, which returns the incorrect IP address.
This redirects the user’s traffic to a website controlled by the attacker, where they can steal sensitive information or launch further attacks.
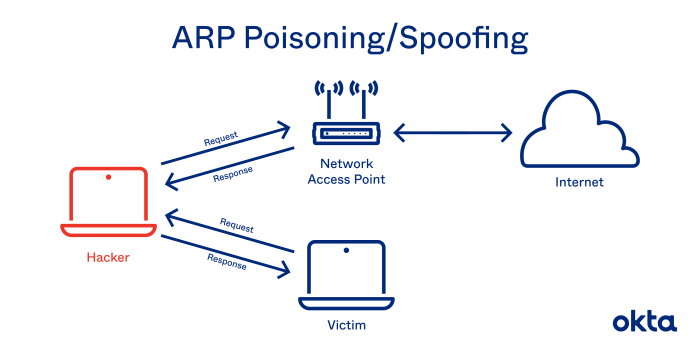
In ARP poisoning, attackers send malicious ARP messages to a target device, claiming to have a specific IP address. The target device updates its ARP cache with the incorrect MAC address, causing subsequent traffic intended for the legitimate device to be misdirected to the attacker’s device.
Common Targets and Vulnerabilities
DNS and ARP poisoning attacks often target critical infrastructure, such as banks, government agencies, and large corporations. These organizations rely heavily on network connectivity and are attractive targets for attackers seeking to disrupt services or steal sensitive data.
Vulnerabilities that make DNS and ARP poisoning possible include:
- DNS servers with weak security measures, such as default passwords or unpatched software.
- ARP caches that are not properly protected, allowing attackers to send malicious ARP messages.
- Network devices with outdated firmware or unpatched operating systems.
Attackers exploit these vulnerabilities by gaining access to the targeted network, either through social engineering or by exploiting known vulnerabilities in network devices.
Detection and Mitigation Techniques

Detecting DNS and ARP poisoning attacks can be challenging, as they often appear as legitimate network traffic. However, there are several techniques that can help identify these attacks:
- Monitoring DNS logs for suspicious activity, such as changes to DNS records or unauthorized access.
- Using ARP scanning tools to detect duplicate or conflicting MAC addresses.
- Implementing intrusion detection systems (IDS) and intrusion prevention systems (IPS) to detect and block malicious network traffic.
Mitigating DNS and ARP poisoning attacks involves:
- Strengthening DNS server security by using strong passwords, patching software, and implementing access control measures.
- Protecting ARP caches by using static ARP entries or implementing ARP filtering.
- Keeping network devices up to date with the latest firmware and operating system updates.
Impact on Network Security: Both Dns Poisoning And Arp Poisoning Involves
DNS and ARP poisoning attacks can have a significant impact on network security, including:
- Data breaches: Attackers can redirect traffic to malicious websites that steal sensitive information, such as login credentials, credit card numbers, and personal data.
- Service disruptions: By redirecting traffic away from legitimate servers, attackers can disrupt critical services, such as email, websites, and online banking.
- Malware infections: Attackers can use DNS and ARP poisoning to distribute malware, such as ransomware or spyware, to target devices.
In 2016, a DNS poisoning attack against the Ukrainian power grid caused a widespread blackout, leaving hundreds of thousands of people without power. Another example is the 2018 ARP poisoning attack against a cryptocurrency exchange, which resulted in the theft of millions of dollars in digital currency.
Comparison of DNS and ARP Poisoning
| DNS Poisoning | ARP Poisoning | |
|---|---|---|
| Attack Mechanism | Manipulates DNS records to redirect traffic | Sends malicious ARP messages to link MAC addresses to incorrect IP addresses |
| Target | DNS servers | ARP caches |
| Impact | Data breaches, service disruptions, malware infections | Data breaches, service disruptions, network access control |
| Mitigation Techniques | Strengthen DNS server security, monitor DNS logs | Protect ARP caches, use static ARP entries |
DNS poisoning and ARP poisoning are both serious network attacks that can have a significant impact on network security. Understanding the mechanisms, vulnerabilities, and mitigation techniques for these attacks is essential for organizations to protect their networks and data.
General Inquiries
What is the difference between DNS poisoning and ARP poisoning?
DNS poisoning targets the Domain Name System (DNS), while ARP poisoning targets the Address Resolution Protocol (ARP).
What are the common vulnerabilities exploited by DNS and ARP poisoning attacks?
DNS poisoning attacks exploit vulnerabilities in DNS servers and client systems, while ARP poisoning attacks exploit vulnerabilities in ARP protocol implementations and network configurations.
How can I detect DNS and ARP poisoning attacks?
DNS poisoning attacks can be detected by monitoring DNS traffic for suspicious activity, while ARP poisoning attacks can be detected by monitoring ARP traffic for inconsistencies.